This section explains how to connect to and interact with Pawsey supercomputing systems.
Prerequisites
To access a supercomputer, users have a Pawsey account, comprising a username and a password. The account must also be a member of an active project allocation on the selected supercomputer. For new users, an account creation email with instructions is sent when you receive an allocation or are added to a project.
Introduction
Pawsey supercomputers are accessed remotely through the SSH protocol. Most of the time users employ the ssh command-line tool installed on their computers, which allows executing commands through a terminal window; other programs implementing the SSH protocol may be used. To execute programs that display a graphical interface you can use X forwarding over SSH.
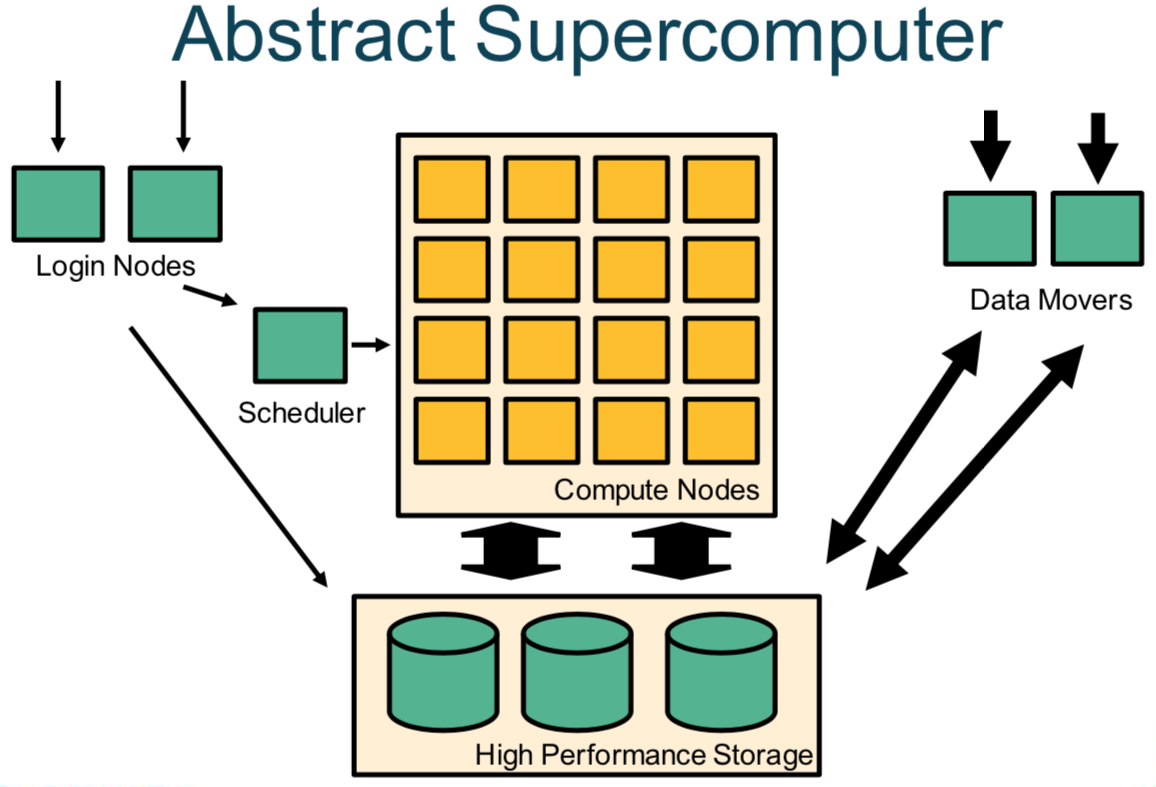
When a connection is established with any of our systems, it is to a login node. Login nodes are the "front desk" of the system, and they allow users to manage their workflows, edit files, and submit jobs to the scheduler to be executed on the compute nodes. The compute nodes are where the main computations are processed and they can be accessed through the different queues or partitions managed by the scheduler. These concepts are illustrated in figure 1.
Figure 1. An abstract overview of a supercomputer architecture
Use SSH to connect to a supercomputer
The login node of a Pawsey supercomputer is reachable through the Internet at an assigned public hostname. The hostname of the login nodes of each Pawsey's supercomputer is listed in table 1. The linux command ssh should be used by users to connect to the login node of a remote host, as shown in the following line.
$ ssh [options] <username>@<hostname>
Replace <username> with the username of your Pawsey account, and <hostname> with one of the hostnames listed in table 1.
Table 1. List of Pawsey's supercomputing systems' hostnames.
| System | Hostname |
|---|---|
| Setonix | setonix.pawsey.org.au |
| Topaz | topaz.pawsey.org.au |
| Garrawarla | garrawarla.pawsey.org.au |
| Data Mover | data-mover.pawsey.org.au |
All Linux and macOS distributions come installed with a terminal application that can be used for SSH access to the login nodes.
- Linux users have different terminals available depending on which distribution and window manager they use (for example: GNOME Terminal in GNOME; Konsole in KDE).
Consult your Linux distribution's documentation for details on how to load a terminal.
- On macOS you can use the Terminal application, which is located in the Utilities folder within the Applications folder.
Another popular terminal application for MacOS is iTerm2, which needs to be installed separately.
The Microsoft Windows operating system now has in-built SSH client support. It may first need to be enabled as an optional feature in the settings. When using the client at the Windows command prompt or PowerShell, the correct MAC option must also be provided:
$ ssh -m hmac-sha2-512 [options] <username>@<hostname>
Alternatively, the line MACs hmac-sha2-512 can be added to a file called config that can be created in the C:\Users\<username>\.ssh directory in Windows to avoid providing this option every time.
It does not currently support X forwarding of graphical interfaces, for which use of the MobaXterm client is recommended.
To authenticate the connection, a user can either enter the password for each connection or use an SSH key. SSH keys provide more security and eliminate the need to enter the password each time the ssh command is executed.
An SSH key is an access credential in the SSH protocol. Its function is similar to that of username and password but enables automated processes and single sign-on users.
Login nodes
The hostname of a supercomputing system is often a pseudonym of several login nodes that the system may have. When connecting remotely, connections are randomly placed on a login node from where you interact with the rest of the system using a round-robin DNS technique. The actual hostname of the login node ("setonix-1" in the example below) can be easily obtained by executing the hostname Linux command after an SSH connection has been established. Terminal 1 illustrates an SSH connection to a login node and outputting the hostname.
$ ssh username@setonix.pawsey.org.au Password: Last login: Mon Jan 10 11:07:13 2022 from 130.116.145.55 ############################################################################## # Pawsey Supercomputing Centre # # Empowering cutting-edge research for Australia's future # # # # This service is for authorised clients only. # # It is a criminal offence to: # # - Obtain access to data without permission # # - Damage, delete, alter or insert data without permission # # # ############################################################################## . . . =============================================================================== By using Pawsey facilities you agree to the Conditions of use available at https://support.pawsey.org.au/documentation/display/US/Conditions+of+Use =============================================================================== username@setonix-1:~> hostname setonix-1